Flair Data Systems Cybersecurity News Update 2-21-2024
My name is Brent Forrest and I serve as a vCISO at Flair Data Systems. Here is your cybersecurity news update for 2/21/2024.
The past couple of days has been a bit of a rollercoaster with the news around LockBit systems being compromised by law enforcement agencies across the world.
Last week I mentioned an article related to "network connected toothbrush bots" and that story is still undetermined in its authenticity. In one hand, Fortinet stated it was hypothetical and not a true incident. However, the journalist is fighting back against that statement and what they were told by Fortinet. On top of that, Fortinet had to release several vulnerabilities last week – I am sure it felt like a monsoon for Fortinet last week.
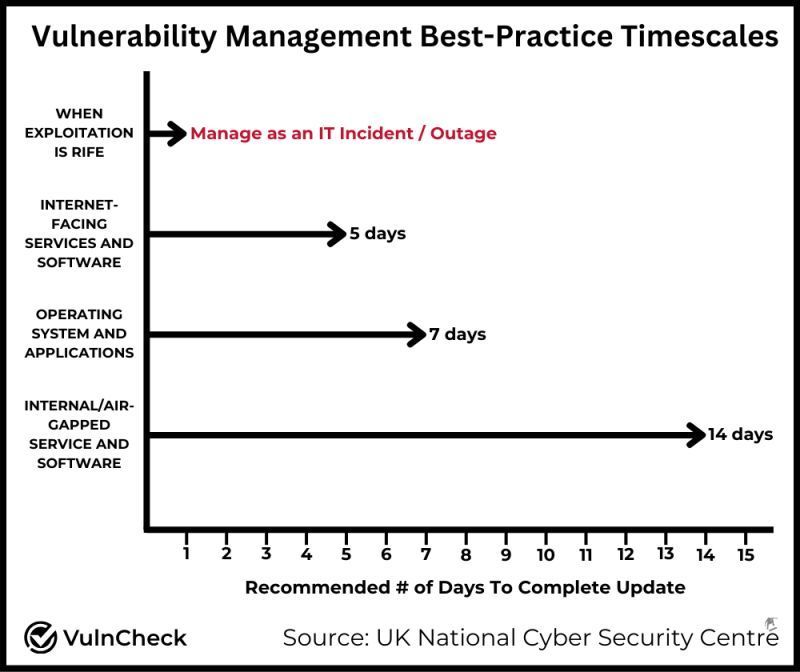
Lastly, I provided a screenshot of how to approach vulnerability patching with the world we live in (included screenshot once more for reference) and I would like to clarify, this is something every organization will have to consider. Some say it is too aggressive - probably so. Some say just focus on Zero-Day / Critical - sounds like a great start. The point is that we are living in a world where threat actors are taking advantage of discovered vulnerabilities sometimes much faster than the vendor can patch them. Do not make changes based on one person's perspective, and do not live in an echo chamber. Determine what is the best fit for the organization you are supporting and requirements around business/compliance/regulations.
With that, let’s jump into this week’s cyber security news update.
LockBit disrupted by global police operation
Operation Cronos, a joint operation between law agencies across 10 countries, has disrupted the LockBit ransomware operation
- National Crime Agency of the United Kingdom has modified the banner on the data leak website to show they have gained control of the site, including the negotiation sites
- Other components of LockBits sites are still operating (data hosting and private message platform)
- Other items that were seized included: LockBit source code, chats, victim information
- Updated to include over 1,000 decryption keys, 34 servers, and over 200 cyrpto-wallets
- Link 3 is a portal that contains Decryption Tools for those that are affected by various threat actors
- Two operators of LockBit were arrested in Poland and Ukraine
- Three international warrants and five indictments targeting other members of LockBit
Link (3): https://www.nomoreransom.org/en/index.html
Trans-Northern Pipelines (TNPI) confirms cyberattack
Breached in November of 2023 by ALPHV/BlackCat ransomware gang
- TNPI operates over 528 miles of pipeline in Ontario-Quebec and 198 miles in Alberta transporting over 221,000 barrels daily
- Pipelines transport gasoline, diesel fuel, aviation fuel, and heating fuel from refineries to distribution terminals
- ALPHV has claimed to have stolen 183GB of documents from the breach
ALPHV gang takes credit for LoanDepot, Prudential attacks
On Feb 16, both Prudential and LoanDepot were listed on ALPHV leak site
- LoanDepots is pending ALPHV potentially selling the data - 16.6 million people personal information stolen
- Prudential's data is looked to be released for free after failed negotiations, and has yet to find evidence that the attacker had actually exfiltrated customer or client data
Threat actors using LLMs to improve cyberattacks
LLM (Large Language Models) for those not familiar with the term is essentially what OpenAI or Gemini (Google) AI based chats are based upon
- Threat actors are weaponizing LLM's to perform reconnaissance, such as learning about potential victims' industries, locations, and relationships
- Five nation-States threat actors weaponizing AI
- Forest Blizzard - Russia
- Emerald Sleet - North Korea
- Crimson Sandstorm - Iran
- Charcoal Typhoon - China
- Salmon Typhoon - China
Google Chrome feature blocks attacks against home networks
Starting in Chrome 123, Google has proposed implementing a "Private Network Access protections" feature - starting out in a "warning-only" mode
- This new feature will conduct checks before a public website directs a browser to visit another site within the user's private network
- The check includes verifying if the request comes from a secure context and sending a preliminary request to see if the internal site permits access from a public website through specific requests called CORS-preflight requests
- The intent for this change is to prevent malicious websites on the internet from exploiting flaws on devices or servers in users' internal networks
Mastermind behind Zeus and IcedID malware pleads guilty
Vyacheslav Igorevich Penchukov (aka Tank) was on the FBI's Cyber Most Wanted List until 2022, where he was arrested in Switzerland
- He was extradited to the US last year and has pleaded guilty to RICO and wire fraud charges related to his leadership role in separate cybercrime operations involving the Zeus and IcedID malware
- Zeus operations started in May 2009 - infecting millions of devices, including thousands of business computers, enabling threat actors to obtain personal and banking information that was capable of being used to make unauthorized transfers from victims' bank accounts
- IcedID operations existed between November 2018 and February 2021 - allowing threat actors to steal banking and personal information, and could also be used to deliver other malware to compromised computers, including ransomware
- Vyacheslav sentencing is scheduled for May 9th and faces up to 20 years in prison for each count
Air Canada must honor refund invented by its chatbot, says court
Jake Moffatt used Air Canada's chatbot to explain how the bereavement rates worked after finding out that his grandmother passed away
- The chatbot provided inaccurate information, encouraging Moffatt to book a flight immediately and then request a refund within 90 days
- However, Air Canada's policy explicitly stated that the airline will not provide refunds for bereavement travel after the flight is booked
- After months of fighting between Moffatt and Air Canada through small claims courts (Canada's Civil Resolution Tribunal), and the case was found in favor of Moffatt
- The Tribunal member stated that "Air Canada argues it cannot be held liable for information provided by one of its agents, servants, or representatives - including a chatbot"
- This is something every organization needs to take into consideration when standing up chatbots to assist their customers, because that chatbot is speaking on behalf of the organization
Link (1): https://www.wired.com/story/air-canada-chatbot-refund-policy/
Cactus leaks Schneider Electric data on dark web
Last month, it was announced that subsidiary of Schneider Electric - Sustainability Business division was comprised
- Cactus ransomware gang has claimed to have stolen 1.5TB of data from Schneider, 25MB of it was leaked on the operations' dark web leak site as proof of life
- It is still unknown what specific data was stolen - but based on the compromised systems that the potential for sensitive information about customers' industrial control and automation systems and information about environmental and energy regulations compliance is a concern
Wyze camera - Incident leading to accidently user view
In September 2023, Wyze users reported that they were seeing camera feeds that were not theirs, which was found to be a Web caching problem
- Last Friday (Feb 16, 2024), this situation occurred again but on a larger scale - 13,000 users received thumbnails from cameras that were not theirs, and 1,504 of those users enlarged the image
- Consumers of Wyze went to Reddit to report the situation, where people were seeing things such as "a stranger's porch", "someone else's living room", and other footages from a different time zone
- The issue was around an AWS outage that occurred early Friday morning and the Wyze servers were overloaded, which resulted in it corrupting some user data (AWS did not report an outage during the time frame of the issues)
- There are multiple concerns here, and it's not my place to judge where one person places a camera vs another person - but this is the very reason you won't find a web-based camera like this within my home. The number of IoT based tools people are bringing into their homes has expanded dramatically and continues to do so every year. One question I like to ask people is "Do you know every device on your home wireless network?" most have no clue.
Link (1): https://www.darkreading.com/endpoint-security/wyze-cameras-allow-accidental-user-spying
Until next week, it’s Brent Forrest signing off. Be cyber safe my friends!
About the Author: Brent Forrest is a Field CISO with Flair Data Systems. In this role, Brents acts as an advisor to customers that span across different verticals providing guidance to include; developing strategies to reduce risk with existing or modern technology while enabling the business. With over 20 years of experience in the IT industry, Brent has been able to be a part of multiple groups within the IT field spanning from Telecom, Network, Wireless, Infrastructure, and eventually finding his passion within Security. Roughly 20 years of that time was spent within the Oil and Gas industry working across multiple teams and leading initiatives. Specifically with EnLink Midstream, he spent most of his time building resilience and developing the cybersecurity program.
Brent has been with Flair Data for 3 years and is CISSP, C|CISO, CvCISO, & Sec+ certified. In his free time, he likes to spend time with family, working out, or staying up with personal development. He lives in Dallas, Texas with his wife and children.
About: Flair Data Systems is a strategically priced IT solutions company, serving clients in the U.S., with offices in Texas and Colorado. Now a technology industry leader, we began in 1916 as the Porter Burgess Company. Flair Data Systems is your Trusted Advisor for: Collaboration, Unified Communications, Networking, Cloud, Infrastructure, Data Analytics, and Cybersecurity, serving the U.S. We provide trusted cyber security services in Plano, TX.





