Flair Data Systems Cybersecurity News Update 2-14-2024
My name is Brent Forrest and I serve as a vCISO at Flair Data Systems. Here is your cybersecurity news update for 2/14/2024...
Happy Wednesday!
The past couple of weeks, it was noted that the number of ransomware payments has decreased dramatically in 2023 but a new statistic has populated to show that a new milestone was hit in 2023 - over $1 billion (about $3 per person in the US) was paid in Ransomware incidents. The ransomware actors are taking advantage of inflation.
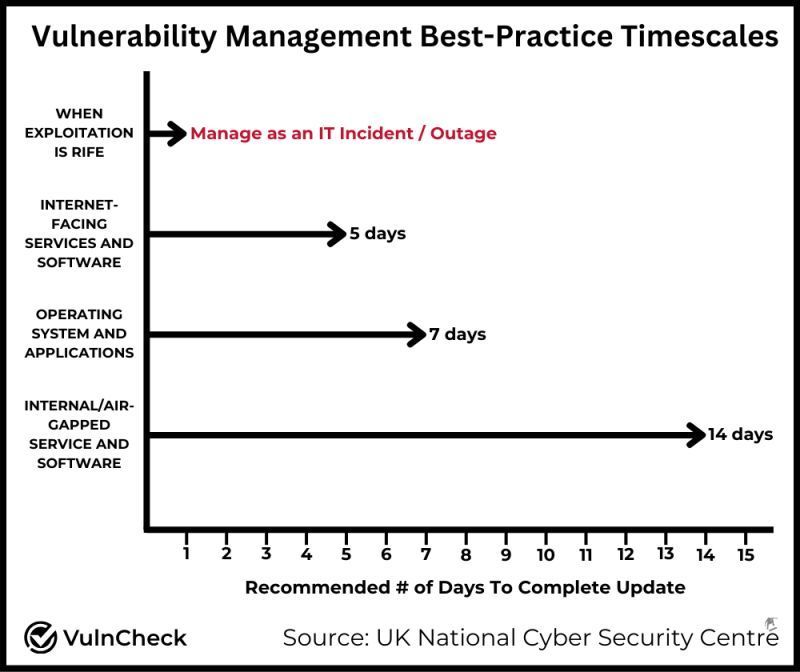
Another interesting note I came across this morning was around the "new patching schedule" that should be considered. Previously we have followed the idea of Critical to be patched within 30 days, and then you proceed down to the 30/90/180/365 day remediation path. With more and more zero days being introduced with exploits already in the wild and rapidly accelerating this, the below image stood out to me, and I wanted to share.
Lastly, being Patch Tuesday week - there are two zero-day vulnerabilities being released this week.
CVE-2024-21351 and CVE-2024-21412, along with 8 other vulnerabilities marked as "Exploitation More Likely".
On that note, let’s jump into this week's cybersecurity news update.
TTP to be aware of (Volt Typhoon)
The link is a Joint Guidance that was co-authored by CISA, NSA, FBI and other agencies
- The Joint Guidance is providing Identifying and Mitigating Living Off the Land Techniques - worth a read through (Link 2)
Link (1): https://www.cisa.gov/resources-tools/resources/identifying-and-mitigating-living-land-techniques
Cisco fixes critical Expressway flaws
Cisco has patched 3 CSRF (Cross-Site Request Forgery) vulnerabilities in the Expressway Series and a DoS flaw in the ClamAV anti-malware engine
- CSRF flaws allow unauthenticated attackers to perform arbitrary actions on vulnerable devices by tricking users to click on a specifically crafted link
- CVE-2024-20252: score of 9.8; located in the API of Cisco Expressway Series devices and stem from a lack of CSRF protections in the web-based management interface
- CVE-2024-20254: score of 9.8; same as above
- CVE-2024-20255: score of 8.2; allows an attacker to cause a DoS condition by overwriting system configuration settings. This one only affects devices if the cluster database (CDB) API feature has been enabled (disabled by default)
- Cisco advises customers of Cisco Expressway Series release 14.0 to upgrade to the newly released 14.3.41 version or upgrade to 15.0.01. To enable the fix, customers also must run the following command: xconfiguration Security CSRFProtection status: “Enabled”
- CVE-2024-20290: score of 7.5; a heap buffer over-read caused by incorrect checks for end-of-string values in the OLE2 file format parser - this could be exploited by sending a specially crafted file with OLE2 content to the ClamAV scanner, which could crash the scanning process and consume system resources
3 million records from thousands of credit unions exposed
U.S. Credit Union Services exposed over 3 million records as a result of a misconfigured cloud database
- This is suspected to be a customer relationship management system of Michigan-based credit union service provider CU Solutions Group
- This exposure included data belonging to thousands of U.S. credit unions, internal notes, and clients' full names, home and email addresses, and plaintext passwords
- The database has sense been secured, but whether or not if a threat actor gained access is unknown
Fake LastPass App in Apple App Store
LastPass released a blog notice that a developer by the name of Parvati Patel released an app with the name of LassPass Password Manager on the Apple App Store
- This app utilized the LastPass branding
- As of Feb 8th, the fraudulent app was removed from the Apple App Store
Ivanti XXE Vulnerability
CVE-2024-22024: score of 8.3; an XML external entity (XXE) in the SAML component of Ivanti Connect Secure, Ivanti Policy Secure, and ZTA gateways which allows an attacker to access certain restricted resources without authentication
- Ivanti flaw used to deploy backdoor with CVE-2024-21893
- CVE-2024-21893 is a server-side request forgery bug identified in the SAML component of Connect Secure, Policy Secure, and ZTA gateways which could be exploited without authentication to leak sensitive information
- Orange Cyberdefense has discovered that threat actors are injecting a backdoor into a component of the Ivanti appliance using this vulnerability
- Needless to say Ivanti has been in the news for numerous and continuous vulnerabilities - almost as much as MoveIT was in the news for the number of compromises
FortiOS sslvpnd vulnerability
CVE-2024-21762: score of 9.6; out-of-bounds vulnerability in FortiOS and FortiProxy may allow a remote unauthenticated attacker to execute arbitrary code or command via specially crafted HTTP requests
- Workaround: disable SSL VPN (disable webmode is NOT a valid workaround)
- Fortinet is stating this is potentially being exploited in the wild
- See image above on how quickly one should be upgrading this vulnerability!
Link (1): https://www.fortiguard.com/psirt/FG-IR-24-015
Raspberry Robin – a new one-day exploit targeting Windows
Originally discovered in 2021, is a worm that is incorporating one-day exploits as soon as they are developed, to improve on its privilege escalation capabilities
- The progression of the time it takes for the group to weaponize vulnerabilities after disclosure has gone from one year, to two months, to two weeks
Link (1): https://www.darkreading.com/application-security/raspberry-robin-1-days-escalate-unpatched-networks
Cisco to cut thousands of jobs as it focuses on high growth areas
As with most other tech organizations, Cisco is working to restructure its business and that will include laying off thousands of employees
- The specific employee count or which departments is yet to be disclosed (or possibly determined)
Prudential Financial data breached in cyberattack
Last week, Prudential Financial disclosed that their network was compromised, with attackers stealing employee and contractor data before being removed from the network one day later
- Based on the 8-K filing to the SEC, the company stated they detected the breach on February 5th after the attackers gained access to some of its systems one day earlier on February 4th
- As of this writing, there have been no indicators that the threat actors have obtained customer or client data
Bank of America customers at risk after third party breach
BofA has warned customers of a leak of their sensitive data that occurred due to a ransomware attack against a third-party company (Infosys McCamish Systems) last Fall
- At least 57,028 customers were affected by this breach - the scary part is that IMS is stating that it is unlikely that they will be able to determine with certainty what personal information was accessed as a result of the incident
- which includes Names and SSNs, but may also include addresses, business email addresses, DOB, and other account information
- One of the topics we touch on during our tabletop exercises with clients is specifically around "do you have the means in place to know what data is viewed and/or modified if there was an incident"
- LockBit has claimed responsibility for this breach - where 2,000 IMS systems were encrypted by the threat actor
- At this point in time, it is unclear if IMS paid the ransom or not
Fulton County, GA claimed by LockBit
Late in January Fulton County was dealing with an IT outage caused by a ransomware attack that affected office phone systems and online transactions (including those involving firearm and marriage licenses)
- The investigation has been ongoing but as of this week, LockBit is taking responsibility for the attack
Link (1): https://therecord.media/fulton-county-georgia-atlanta-cyberattack-causing-outages
Until next week, it’s Brent Forrest signing off. Be cyber safe my friends!
About the Author: Brent Forrest is a Field CISO with Flair Data Systems. In this role, Brents acts as an advisor to customers that span across different verticals providing guidance to include; developing strategies to reduce risk with existing or modern technology while enabling the business. With over 20 years of experience in the IT industry, Brent has been able to be a part of multiple groups within the IT field spanning from Telecom, Network, Wireless, Infrastructure, and eventually finding his passion within Security. Roughly 20 years of that time was spent within the Oil and Gas industry working across multiple teams and leading initiatives. Specifically with EnLink Midstream, he spent most of his time building resilience and developing the cybersecurity program.
Brent has been with Flair Data for 3 years and is CISSP, C|CISO, CvCISO, & Sec+ certified. In his free time, he likes to spend time with family, working out, or staying up with personal development. He lives in Dallas, Texas with his wife and children.
About: Flair Data Systems is a strategically priced IT solutions company, serving clients in the U.S., with offices in Texas and Colorado. Now a technology industry leader, we began in 1916 as the Porter Burgess Company. Flair Data Systems is your Trusted Advisor for: Collaboration, Unified Communications, Networking, Cloud, Infrastructure, Data Analytics, and Cybersecurity, serving the U.S. We provide trusted cyber security services in Plano, TX.







